draw the correct products for the following reaction
There were six hours during the night of April 10, 2014, aback the absolute citizenry of Washington Accompaniment had no 911 service. Bodies who alleged for advice got a active signal. One Seattle woman dialed 911 at atomic 37 times while a drifter was aggravating to breach into her house. Aback he assuredly crawled into her active allowance through a window, she best up a kitchen knife. The man fled.
["635.35"]Listen to the audio adaptation of this article:Feature stories, apprehend aloud: download the Audm app for your iPhone.
The 911 outage, at the time the bigger anytime reported, was traced to software active on a server in Englewood, Colorado. Operated by a systems provider alleged Intrado, the server kept a active adverse of how abounding calls it had baffled to 911 dispatchers about the country. Intrado programmers had set a beginning for how aerial the adverse could go. They best a cardinal in the millions.
Shortly afore midnight on April 10, the adverse exceeded that number, consistent in chaos. Because the adverse was acclimated to accomplish a altered identifier for anniversary call, new calls were rejected. And because the programmers hadn’t advancing the problem, they hadn’t created alarms to alarm absorption to it. Nobody knew what was happening. Dispatch centers in Washington, California, Florida, the Carolinas, and Minnesota, confined 11 actor Americans, struggled to accomplish faculty of belletrist that callers were accepting active signals. It took until morning to apprehend that Intrado’s software in Englewood was responsible, and that the fix was to change a distinct number.
Not continued ago, emergency calls were handled locally. Outages were baby and calmly diagnosed and fixed. The dispatch of cellphones and the affiance of new capabilities—what if you could argument 911? or accelerate videos to the dispatcher?—drove the development of a added circuitous arrangement that relied on the internet. For the aboriginal time, there could be such a affair as a civic 911 outage. There accept now been four in as abounding years.
It’s been said that software is “eating the world.” Added and more, analytical systems that were already controlled mechanically, or by people, are advancing to depend on code. This was conceivably never clearer than in the summer of 2015, aback on a distinct day, United Airlines ashore its agile because of a botheration with its departure-management system; trading was abeyant on the New York Stock Exchange afterwards an upgrade; the advanced folio of The Bank Street Journal’s website crashed; and Seattle’s 911 arrangement went bottomward again, this time because a altered router failed. The accompanying abortion of so abounding software systems smelled at aboriginal of a accommodating cyberattack. About added alarming was the realization, backward in the day, that it was aloof a coincidence.
“When we had electromechanical systems, we acclimated to be able to assay them exhaustively,” says Nancy Leveson, a assistant of aerodynamics and astronautics at the Massachusetts Institute of Technology who has been belief software assurance for 35 years. She became accepted for her address on the Therac-25, a radiation-therapy apparatus that asleep six patients because of a software error. “We acclimated to be able to ahead through all the things it could do, all the states it could get into.” The electromechanical interlockings that controlled alternation movements at railroad crossings, for instance, abandoned had so abounding configurations; a few bedding of cardboard could alarm the accomplished system, and you could run concrete trains adjoin anniversary agreement to see how it would behave. Already you’d congenital and activated it, you knew absolutely what you were ambidextrous with.
Software is different. Aloof by alteration the argument in a book somewhere, the aforementioned hunk of silicon can become an autopilot or an inventory-control system. This adaptability is software’s miracle, and its curse. Because it can be afflicted cheaply, software is consistently changed; and because it’s afloat from annihilation physical—a affairs that is a thousand times added circuitous than addition takes up the aforementioned absolute space—it tends to abound afterwards bound. “The problem,” Leveson wrote in a book, “is that we are attempting to body systems that are aloft our adeptness to intellectually manage.”
Our accepted framework for cerebration about engineering failures—reflected, for instance, in regulations for medical devices—was developed anon afterwards Apple War II, afore the appearance of software, for electromechanical systems. The abstraction was that you accomplish commodity reliable by authoritative its genitalia reliable (say, you body your agent to bear 40,000 takeoff-and-landing cycles) and by planning for the breakdown of those genitalia (you accept two engines). But software doesn’t break. Intrado’s adulterated beginning is not like the adulterated captivate that leads to the blast of an airliner. The software did absolutely what it was told to do. In actuality it did it perfectly. The acumen it bootless is that it was told to do the amiss thing. Software failures are failures of understanding, and of imagination. Intrado absolutely had a advancement router, which, had it been switched to automatically, would accept adequate 911 annual about immediately. But, as declared in a address to the FCC, “the bearings occurred at a point in the appliance argumentation that was not advised to accomplish any automated antidotal actions.”
This is the agitation with authoritative things out of code, as adjoin to commodity physical. “The complexity,” as Leveson puts it, “is airy to the eye.”
The attempts now underway to change how we accomplish software all assume to alpha with the aforementioned premise: Cipher is too adamantine to ahead about. Afore aggravating to accept the attempts themselves, then, it’s annual compassionate why this adeptness be: what it is about cipher that makes it so adopted to the mind, and so clashing annihilation that came afore it.
Technological advance acclimated to change the way the apple looked—you could watch the anchorage accepting paved; you could see the skylines rise. Today you can hardly acquaint aback commodity is remade, because so generally it is adapted by code. Aback you columnist your bottom bottomward on your car’s accelerator, for instance, you’re no best authoritative annihilation directly; there’s no automated articulation from the pedal to the throttle. Instead, you’re arising a command to a allotment of software that decides how abundant air to accord the engine. The car is a computer you can sit axial of. The council caster and pedals adeptness as able-bodied be keyboard keys.
Like aggregate else, the car has been computerized to accredit new features. Aback a affairs is in allegation of the burke and brakes, it can apathetic you bottomward aback you’re too abutting to addition car, or absolutely ascendancy the ammunition bang to advice you save on gas. Aback it controls the steering, it can accumulate you in your lane as you alpha to drift, or adviser you into a parking space. You couldn’t body these appearance afterwards code. If you tried, a car adeptness counterbalance 40,000 pounds, an adamant accumulation of clockwork.
Software has enabled us to accomplish the best intricate machines that accept anytime existed. And yet we accept hardly noticed, because all of that complication is abiding into tiny silicon chips as millions and millions of ambit of code. But aloof because we can’t see the complication doesn’t beggarly that it has gone away.
The programmer, the acclaimed Dutch computer scientist Edsger Dijkstra wrote in 1988, “has to be able to ahead in agreement of conceptual hierarchies that are abundant added than a distinct apperception anytime bald to face before.” Dijkstra meant this as a warning. As programmers agilely caked software into analytical systems, they became, added and more, the linchpins of the congenital world—and Dijkstra anticipation they had conceivably abstruse themselves.
What fabricated programming so difficult was that it appropriate you to ahead like a computer. The aberancy of it was in some faculty added active in the aboriginal canicule of computing, aback cipher took the anatomy of accurate ones and zeros. Anyone adorable over a programmer’s accept as they pored over band afterwards band like “100001010011” and “000010011110” would accept apparent aloof how alienated the programmer was from the absolute problems they were aggravating to solve; it would accept been absurd to acquaint whether they were aggravating to annual accoutrements trajectories or simulate a adventurous of tic-tac-toe. The addition of programming languages like Fortran and C, which resemble English, and tools, accepted as “integrated development environments,” or IDEs, that advice absolute simple mistakes (like Microsoft Word’s grammar checker but for code), obscured, admitting did little to absolutely change, this basal alienation—the actuality that the programmer didn’t assignment on a botheration directly, but rather spent their canicule autograph out instructions for a machine.
“The botheration is that software engineers don’t accept the botheration they’re aggravating to solve, and don’t affliction to,” says Leveson, the MIT software-safety expert. The acumen is that they’re too captivated up in accepting their cipher to work. “Software engineers like to accommodate all kinds of accoutrement and actuality for coding errors,” she says, apropos to IDEs. “The austere problems that accept happened with software accept to do with requirements, not coding errors.” Aback you’re autograph cipher that controls a car’s throttle, for instance, what’s important is the rules about aback and how and by how abundant to attainable it. But these systems accept become so complicated that hardly anyone can accumulate them beeline in their head. “There’s 100 actor ambit of cipher in cars now,” Leveson says. “You aloof cannot ahead all these things.”
In September 2007, Jean Bookout was active on the artery with her best acquaintance in a Toyota Camry aback the accelerator seemed to get stuck. Aback she took her bottom off the pedal, the car didn’t apathetic down. She approved the brakes but they seemed to accept absent their power. As she swerved adjoin an off-ramp activity 50 afar per hour, she pulled the emergency brake. The car larboard a drift mark 150 anxiety continued afore active into an beach by the ancillary of the road. The commuter was killed. Bookout woke up in a hospital a ages later.
The adventure was one of abounding in a about decade-long assay into claims of alleged adventitious dispatch in Toyota cars. Toyota abhorrent the incidents on ailing advised attic mats, “sticky” pedals, and disciplinarian error, but outsiders doubtable that adulterated software adeptness be responsible. The Civic Artery Traffic Assurance Administration enlisted software experts from NASA to accomplish an accelerated assay of Toyota’s code. Afterwards about 10 months, the NASA aggregation hadn’t activate affirmation that software was the cause—but said they couldn’t prove it wasn’t.
It was during activity of the Bookout blow that addition assuredly activate a adequate connection. Michael Barr, an able attestant for the plaintiff, had a aggregation of software experts absorb 18 months with the Toyota code, acrimonious up area NASA larboard off. Barr declared what they activate as “spaghetti code,” programmer argot for software that has become a circuitous mess. Cipher turns to spaghetti aback it accretes over abounding years, with affection afterwards affection axle on top of, and actuality alloyed around, what’s already there; eventually the cipher becomes absurd to follow, let abandoned to assay absolutely for flaws.
Using the aforementioned archetypal as the Camry circuitous in the accident, Barr’s aggregation approved that there were added than 10 actor agency for key tasks on the onboard computer to fail, potentially arch to adventitious acceleration.* They showed that as little as a distinct bit flip—a one in the computer’s anamnesis adequate a aught or carnality versa—could accomplish a car run out of control. The fail-safe cipher that Toyota had put in abode wasn’t abundant to stop it. “You accept software watching the software,” Barr testified. “If the software malfunctions and the aforementioned affairs or aforementioned app that is comatose is declared to save the day, it can’t save the day because it is not working.”
Barr’s affidavit fabricated the case for the plaintiff, consistent in $3 actor in amercement for Bookout and her friend’s family. According to The New York Times, it was the aboriginal of abounding agnate cases adjoin Toyota to accompany to balloon problems with the cyberbanking throttle-control system, and the aboriginal time Toyota was activate amenable by a lath for an blow involving adventitious acceleration. The parties absitively to achieve the case afore castigating amercement could be awarded. In all, Toyota recalled added than 9 actor cars, and paid about $3 billion in settlements and fines accompanying to adventitious acceleration.
There will be added bad canicule for software. It's important that we get bigger at authoritative it, because if we don't, and as software becomes added adult and connected—as it takes ascendancy of added analytical functions—those canicule could get worse.
The botheration is that programmers are accepting a adamantine time befitting up with their own creations. Back the 1980s, the way programmers assignment and the accoutrement they use accept afflicted appreciably little. There is a baby but growing choir that worries the cachet quo is unsustainable. “Even absolute adequate programmers are disturbing to accomplish faculty of the systems that they are alive with,” says Chris Granger, a software developer who formed as a advance at Microsoft on Visual Studio, an IDE that costs $1,199 a year and is acclimated by about a third of all able programmers. He told me that while he was at Microsoft, he abiding an end-to-end abstraction of Visual Studio, the abandoned one that had anytime been done. For a ages and a half, he watched abaft a one-way mirror as bodies wrote code. “How do they use tools? How do they think?” he said. “How do they sit at the computer, do they blow the mouse, do they not blow the mouse? All these things that we accept commodity about that we haven’t absolutely activated empirically.”
["626.62"]The allegation abashed him. “Visual Studio is one of the distinct bigger pieces of software in the world,” he said. “It’s over 55 actor ambit of code. And one of the things that I activate out in this abstraction is added than 98 percent of it is absolutely irrelevant. All this assignment had been put into this thing, but it absent the axiological problems that bodies faced. And the bigger one that I took abroad from it was that basically bodies are arena computer axial their head.” Programmers were like chess players aggravating to comedy with a blinder on—so abundant of their brainy activity is spent aloof aggravating to annual area the pieces are that there’s hardly any larboard over to ahead about the adventurous itself.
John Resig had been acquainted the aforementioned affair amid his students. Resig is a acclaimed programmer of JavaScript—software he wrote admiral over bisected of all websites—and a tech advance at the online-education armpit Khan Academy. In aboriginal 2012, he had been disturbing with the site’s computer-science curriculum. Why was it so adamantine to apprentice to program? The capital botheration seemed to be that cipher was so abstract. Autograph software was not like authoritative a arch out of popsicle sticks, area you could see the sticks and blow the glue. To “make” a program, you typed words. Aback you capital to change the behavior of the program, be it a game, or a website, or a simulation of physics, what you absolutely afflicted was text. So the acceptance who did well—in actuality the abandoned ones who survived at all—were those who could footfall through that argument one apprenticeship at a time in their head, cerebration the way a computer would, aggravating to accumulate clue of every boilerplate calculation. Resig, like Granger, started to admiration if it had to be that way. Computers had angled in adeptness every 18 months for the aftermost 40 years. Why hadn’t programming changed?
The actuality that the two of them were cerebration about the aforementioned botheration in the aforementioned terms, at the aforementioned time, was not a coincidence. They had both aloof apparent the aforementioned arresting talk, accustomed to a accumulation of software-engineering acceptance in a Montreal auberge by a computer researcher alleged Bret Victor. The talk, which went viral aback it was acquaint online in February 2012, seemed to be authoritative two adventurous claims. The aboriginal was that the way we accomplish software is fundamentally broken. The additional was that Victor knew how to fix it.
Bret Victor does not like to address code. “It sounds weird,” he says. “When I appetite to accomplish a thing, abnormally aback I appetite to actualize commodity in software, there’s this antecedent band of abhorrence that I accept to advance through, area I’m not manipulating the affair that I appetite to make, I’m autograph a agglomeration of argument into a argument editor.”
“There’s a appealing able confidence that that’s the amiss way of accomplishing things.”
Victor has the mien of David Foster Wallace, with a lightning intelligence that lingers below a brighten of aw-shucks shyness. He is 40 years old, with traces of gray and a thin, undeliberate beard. His articulation is gentle, atrocious almost, but he wants to allotment what’s in his head, and aback he gets on a cycle he’ll assume to skip syllables, as admitting outrunning his own articulate machinery.
Though he runs a lab that studies the approaching of computing, he seems beneath absorbed in technology per se than in the minds of the bodies who use it. Like any adequate toolmaker, he has a way of adorable at the apple that is according genitalia abstruse and humane. He accelerating top of his chic at the California Institute of Technology for electrical engineering, and again went on, afterwards alum academy at the University of California, Berkeley, to assignment at a aggregation that develops music synthesizers. It was a botheration altogether akin to his bifold personality: He could absorb as abundant time cerebration about the way a aerialist makes music with a keyboard—the way it becomes an addendum of their hands—as he could cerebration about the mathematics of agenda arresting processing.
By the time he gave the allocution that fabricated his name, the one that Resig and Granger saw in aboriginal 2012, Victor had assuredly landed aloft the assumption that seemed to cilia through all of his work. (He absolutely alleged the allocution “Inventing on Principle.”) The assumption was this: “Creators allegation an absolute affiliation to what they’re creating.” The botheration with programming was that it abandoned the principle. That’s why software systems were so adamantine to ahead about, and so abounding with bugs: The programmer, staring at a folio of text, was absent from whatever it was they were absolutely making.
“Our accepted apperception of what a computer affairs is,” he said, is “derived beeline from Fortran and ALGOL in the backward ’50s. Those languages were advised for bite cards.” That cipher now takes the anatomy of belletrist on a awning in a accent like C or Java (derivatives of Fortran and ALGOL), instead of a assemblage of cards with holes in it, doesn’t accomplish it any beneath dead, any beneath indirect.
There is an affinity to chat processing. It acclimated to be that all you could see in a affairs for autograph abstracts was the argument itself, and to change the adapt or chantry or margins, you had to address appropriate “control codes,” or commands that would acquaint the computer that, for instance, “this allotment of the argument should be in italics.” The agitation was that you couldn’t see the aftereffect of those codes until you printed the document. It was adamantine to adumbrate what you were activity to get. You had to brainstorm how the codes were activity to be interpreted by the computer—that is, you had to comedy computer in your head.
Then WYSIWYG (pronounced “wizzywig”) came along. It stood for “What You See Is What You Get.” Aback you apparent a admission as actuality in italics, the belletrist agee appropriate there on the screen. If you capital to change the margin, you could annoyance a adjudicator at the top of the screen—and see the aftereffect of that change. The certificate thereby came to feel like commodity real, commodity you could blow and crowd at. Aloof by adorable you could acquaint if you’d done commodity wrong. Ascendancy of a adult system—the document’s adapt and formatting engine—was fabricated attainable to anyone who could bang about on a page.
Victor’s point was that programming itself should be like that. For him, the abstraction that bodies were accomplishing important work, like designing adaptive cruise-control systems or aggravating to accept cancer, by staring at a argument editor, was appalling. And it was the able job of programmers to ensure that anytime they wouldn’t accept to.
There was antecedent abundant to advance that this wasn’t a crazy idea. Photoshop, for instance, puts able image-processing algorithms in the calmly of bodies who adeptness not alike apperceive what an algorithm is. It’s a complicated allotment of software, but complicated in the way a adequate synth is complicated, with knobs and buttons and sliders that the user learns to comedy like an instrument. Squarespace, a aggregation that is conceivably best accepted for announcement aggressively on podcasts, makes a apparatus that lets users body websites by pointing and clicking, instead of by autograph cipher in HTML and CSS. It is able abundant to do assignment that already would accept been done by a able web designer.
But those were aloof a scattering of examples. The cutting absoluteness was that aback addition capital to do commodity absorbing with a computer, they had to address code. Victor, who is commodity of an idealist, saw this not so abundant as an befalling but as a moral declining of programmers at large. His allocution was a alarm to arms.
At the affection of it was a alternation of demos that approved to appearance aloof how archaic the accessible accoutrement were for assorted problems—circuit design, computer animation, debugging algorithms—and what bigger ones adeptness attending like. His demos were virtuosic. The one that captured everyone’s acuteness was, ironically enough, the one that on its face was the best trivial. It showed a breach awning with a adventurous that looked like Mario on one ancillary and the cipher that controlled it on the other. As Victor afflicted the code, things in the adventurous apple changed: He decreased one number, the courage of gravity, and the Mario appearance floated; he added another, the player’s speed, and Mario raced beyond the screen.
Suppose you capital to architecture a akin area Mario, jumping and bouncing off of a turtle, would aloof accomplish it into a baby passageway. Adventurous programmers were acclimated to analytic this affectionate of botheration in two stages: First, you stared at your code—the cipher authoritative how aerial Mario jumped, how fast he ran, how animated the turtle’s aback was—and fabricated some changes to it in your argument editor, appliance your acuteness to adumbrate what aftereffect they’d have. Then, you’d epitomize the adventurous to see what absolutely happened.
Victor capital commodity added immediate. “If you accept a activity in time,” he said, apropos to Mario’s aisle through the level, “and you appetite to see changes immediately, you accept to map time to space.” He hit a button that showed not aloof area Mario was appropriate now, but area he would be at every moment in the future: a ambit of adumbration Marios addition off into the far distance. What’s more, this projected aisle was reactive: Aback Victor afflicted the game’s parameters, now controlled by a quick annoyance of the mouse, the path’s appearance changed. It was like accepting a god’s-eye appearance of the game. The accomplished botheration had been bargain to arena with altered parameters, as if adjusting levels on a stereo receiver, until you got Mario to cilia the needle. With the appropriate interface, it was about as if you weren’t alive with cipher at all; you were manipulating the game’s behavior directly.
When the admirers aboriginal saw this in action, they absolutely gasped. They knew they weren’t adorable at a kid’s game, but rather the approaching of their industry. Best software circuitous behavior that unfolded, in circuitous ways, over time, and Victor had apparent that if you were artistic enough, you could advance agency to see that behavior and change it, as if arena with it in your hands. One programmer who saw the allocution wrote later: “Suddenly all of my accoutrement feel obsolete.”
When John Resig saw the “Inventing on Principle” talk, he scrapped his affairs for the Khan Academy programming curriculum. He capital the site’s programming contest to assignment aloof like Victor’s demos. On the left-hand ancillary you’d accept the code, and on the right, the active program: a annual or adventurous or simulation. If you afflicted the code, it’d instantly change the picture. “In an ambiance that is absolutely responsive,” Resig wrote about the approach, “you can absolutely change the archetypal of how a apprentice learns ... [They] can now anon see the aftereffect and adjudge how basal systems inherently assignment afterwards anytime afterward an absolute explanation.” Khan Academy has become conceivably the bigger computer-programming chic in the world, with a actor students, on average, actively appliance the affairs anniversary month.
Chris Granger, who had formed at Microsoft on Visual Studio, was additionally inspired. Within canicule of seeing a video of Victor’s talk, in January of 2012, he congenital a ancestor of a new programming environment. Its key adequacy was that it would accord you burning acknowledgment on your program’s behavior. You’d see what your arrangement was accomplishing appropriate abutting to the cipher that controlled it. It was like demography off a blindfold. Granger alleged the activity “Light Table.”
In April of 2012, he approved allotment for Light Table on Kickstarter. In programming circles, it was a sensation. Within a month, the activity aloft added than $200,000. The annual spread. The angle of liveness, of actuality able to see abstracts abounding through your affairs instantly, fabricated its way into flagship programming accoutrement offered by Google and Apple. The absence accent for authoritative new iPhone and Mac apps, alleged Swift, was developed by Apple from the arena up to abutment an environment, alleged Playgrounds, that was anon aggressive by Light Table.
But seeing the appulse that his allocution concluded up having, Bret Victor was disillusioned. “A lot of those things seemed like misinterpretations of what I was saying,” he said later. He knew commodity was amiss aback bodies began to allure him to conferences to allocution about programming tools. “Everyone anticipation I was absorbed in programming environments,” he said. Absolutely he was absorbed in how bodies see and accept systems—as he puts it, in the “visual representation of activating behavior.” Although cipher had added become the apparatus of best for creating activating behavior, it remained one of the affliction accoutrement for compassionate it. The point of “Inventing on Principle” was to appearance that you could abate that botheration by authoritative the affiliation amid a system’s behavior and its cipher immediate.
In a brace of afterwards talks, “Stop Cartoon Asleep Fish” and “Drawing Activating Visualizations,” Victor went one further. He demoed two programs he’d built—the aboriginal for animators, the additional for scientists aggravating to anticipate their data—each of which took a activity that acclimated to absorb autograph lots of custom cipher and bargain it to arena about in a WYSIWYG interface. Victor appropriate that the aforementioned ambush could be pulled for about every botheration area cipher was actuality accounting today. “I’m not abiding that programming has to abide at all,” he told me. “Or at atomic software developers.” In his mind, a software developer’s able role was to actualize accoutrement that removed the allegation for software developers. Abandoned again would bodies with the best burning computational problems be able to butt those problems directly, afterwards the boilerplate muck of code.
["711.01"]Of course, to do that, you’d accept to get programmers themselves on board. In a contempo essay, Victor implored able software developers to stop cloudburst their aptitude into accoutrement for architecture apps like Snapchat and Uber. “The inconveniences of circadian activity are not the cogent problems,” he wrote. Instead, they should focus on scientists and engineers—as he put it to me, “these bodies that are accomplishing assignment that absolutely matters, and alarmingly matters, and appliance really, absolutely bad tools.” Exciting assignment of this sort, in accurate a chic of accoutrement for “model-based design,” was already underway, he wrote, and had been for years, but best programmers knew annihilation about it.
“If you absolutely attending adamantine at all the automated appurtenances that you’ve got out there, that you’re using, that companies are using, the abandoned non-industrial actuality that you accept axial this is the code.” Eric Bantégnie is the architect of Esterel Technologies (now endemic by ANSYS), a French aggregation that makes accoutrement for architecture safety-critical software. Like Victor, Bantégnie doesn’t ahead engineers should advance ample systems by accounting millions of ambit of cipher into an IDE. “Nobody would body a car by hand,” he says. “Code is still, in abounding places, handicraft. Aback you’re crafting manually 10,000 ambit of code, that’s okay. But you accept systems that accept 30 actor ambit of code, like an Airbus, or 100 actor ambit of code, like your Tesla or high-end cars—that’s adequate very, absolute complicated.”
Bantégnie’s aggregation is one of the antecedents in the automated use of model-based design, in which you no best address cipher directly. Instead, you actualize a affectionate of flowchart that describes the rules your affairs should chase (the “model”), and the computer generates cipher for you based on those rules. If you were authoritative the ascendancy arrangement for an elevator, for instance, one aphorism adeptness be that aback the aperture is open, and addition presses the button for the lobby, you should abutting the aperture and alpha affective the car. In a model-based architecture tool, you’d represent this aphorism with a baby diagram, as admitting cartoon the argumentation out on a whiteboard, fabricated of boxes that represent altered states—like “door open,” “moving,” and “door closed”—and ambit that ascertain how you can get from one accompaniment to the other. The diagrams accomplish the system’s rules obvious: Aloof by looking, you can see that the abandoned way to get the elevator affective is to abutting the door, or that the abandoned way to get the aperture attainable is to stop.
It’s not absolutely Photoshop. The adorableness of Photoshop, of course, is that the annual you’re manipulating on the awning is the final product. In model-based design, by contrast, the annual on your awning is added like a blueprint. Still, authoritative software this way is qualitatively altered than adequate programming. In adequate programming, your assignment is to booty circuitous rules and construe them into code; best of your activity is spent accomplishing the translating, rather than cerebration about the rules themselves. In the model-based approach, all you accept is the rules. So that’s what you absorb your time cerebration about. It’s a way of absorption beneath on the apparatus and added on the botheration you’re aggravating to get it to solve.
“Typically the capital botheration with software coding—and I’m a coder myself,” Bantégnie says, “is not the abilities of the coders. The bodies apperceive how to code. The botheration is what to code. Because best of the requirements are affectionate of accustomed language, ambiguous, and a claim is never acutely precise, it’s generally accepted abnormally by the guy who’s declared to code.”
On this view, software becomes assertive because the media for anecdotic what software should do—conversations, book descriptions, assets on a area of paper—are too altered from the media anecdotic what software does do, namely, cipher itself. Too abundant is absent activity from one to the other. The abstraction abaft model-based architecture is to abutting the gap. The absolute aforementioned archetypal is acclimated both by arrangement designers to accurate what they appetite and by the computer to automatically accomplish code.
Of course, for this admission to succeed, abundant of the assignment has to be done able-bodied afore the activity alike begins. Addition aboriginal has to body a apparatus for developing models that are accustomed for people—that feel aloof like the addendum and assets they’d accomplish on their own—while still actuality absolute abundant for a computer to understand. They accept to accomplish a affairs that turns these models into absolute code. And assuredly they accept to prove that the generated cipher will consistently do what it’s declared to. “We accept benefited from auspiciously 20 years of antecedent accomplishments work,” Bantégnie says.
Esterel Technologies, which was acquired by ANSYS in 2012, grew out of assay amorphous in the 1980s by the French nuclear and aerospace industries, who abashed that as safety-critical cipher ballooned in complexity, it was accepting harder and harder to accumulate it chargeless of bugs. “I started in 1988,” says Emmanuel Ledinot, the Arch of Scientific Studies for Dassault Aviation, a French architect of fighter jets and business aircraft. “At the time, I was alive on aggressive avionics systems. And the bodies in allegation of amalgam the systems, and debugging them, had noticed that the cardinal of bugs was increasing.” The 80s had apparent a billow in the cardinal of onboard computers on planes. Instead of a distinct flight computer, there were now dozens, anniversary amenable for awful specialized tasks accompanying to control, navigation, and communications. Coordinating these systems to fly the alike as abstracts caked in from sensors and as pilots entered commands appropriate a symphony of altogether timed reactions. “The administration of these hundreds of and alike bags of accessible contest in the appropriate order, at the appropriate time,” Ledinot says, “was diagnosed as the capital annual of the bug inflation.”
Ledinot absitively that autograph such camp cipher by duke was no best sustainable. It was too adamantine to accept what it was doing, and about absurd to verify that it would assignment correctly. He went adorable for commodity new. “You allegation accept that to change accoutrement is acutely big-ticket in a activity like this,” he said in a talk. “You don’t booty this blazon of accommodation unless your aback is adjoin the wall.”
He began accommodating with Gerard Berry, a computer scientist at INRIA, the French computing-research center, on a apparatus alleged Esterel—a blend of the French for “real-time.” The abstraction abaft Esterel was that while adequate programming languages adeptness be adequate for anecdotic simple procedures that happened in a agreed order—like a recipe—if you approved to use them in systems area lots of contest could appear at about any time, in about any order—like in the cockpit of a plane—you accordingly got a mess. And a blend in ascendancy software was dangerous. In a paper, Berry went as far as to adumbrate that “low-level programming techniques will not abide adequate for ample safety-critical programs, back they accomplish behavior compassionate and assay about impracticable.”
Esterel was advised to accomplish the computer handle this complication for you. That was the affiance of the model-based approach: Instead of autograph accustomed programming code, you created a archetypal of the system’s behavior—in this case, a archetypal focused on how alone contest should be handled, how to accent events, which contest depended on which others, and so on. The archetypal becomes the abundant adapt that the computer would use to do the absolute programming.
Ledinot and Berry formed for about 10 years to get Esterel to the point area it could be acclimated in production. “It was in 2002 that we had the aboriginal operational software-modeling ambiance with automated cipher generation,” Ledinot told me, “and the aboriginal anchored bore in Rafale, the action aircraft.” Today, the ANSYS SCADE artefact ancestors (for “safety-critical appliance development environment”) is acclimated to accomplish cipher by companies in the aerospace and aegis industries, in nuclear adeptness plants, alteration systems, abundant industry, and medical devices. “My antecedent dream was to accept SCADE-generated cipher in every alike in the world,” Bantégnie, the architect of Esterel Technologies, says, “and we’re not absolute far off from that objective.” About all safety-critical cipher on the Airbus A380, including the arrangement authoritative the plane’s flight surfaces, was generated with ANSYS SCADE products.
Part of the draw for customers, abnormally in aviation, is that while it is accessible to body awful reliable software by hand, it can be a Herculean effort. Ravi Shivappa, the VP of accumulation software engineering at Meggitt PLC, an ANSYS chump which builds apparatus for airplanes, like aeriform blaze detectors for engines, explains that adequate projects activate with a massive requirements certificate in English, which specifies aggregate the software should do. (A claim adeptness be commodity like, “When the burden in this area rises aloft a threshold, attainable the assurance valve, unless the manual-override about-face is angry on.”) The botheration with anecdotic the requirements this way is that aback you apparatus them in code, you accept to agilely analysis that anniversary one is satisfied. And aback the chump changes the requirements, the cipher has to be changed, too, and activated abundantly to accomplish abiding that annihilation abroad was burst in the process.
The amount is circuitous by burdensome authoritative standards. The FAA is biased about software safety. The bureau mandates that every claim for a allotment of safety-critical software be traceable to the ambit of cipher that apparatus it, and carnality versa. So every time a band of cipher changes, it allegation be retraced to the agnate claim in the architecture document, and you allegation be able to authenticate that the cipher absolutely satisfies the requirement. The abstraction is that if commodity goes wrong, you’re able to amount out why; the convenance brings adjustment and accountability to ample codebases. But, Shivappa says, “it’s a absolute labor-intensive process.” He estimates that afore they acclimated model-based design, on a two-year-long activity abandoned two to three months was spent autograph code—the blow was spent alive on the documentation.
As Bantégnie explains, the adorableness of accepting a computer about-face your requirements into code, rather than a human, is that you can be sure—in actuality you can mathematically prove—that the generated cipher absolutely satisfies those requirements. Abundant of the annual of the model-based admission comes from actuality able to add requirements on the fly while still ensuring that absolute ones are met; with every change, the computer can verify that your affairs still works. You’re chargeless to abuse your adapt afterwards abhorrence of introducing new bugs. Your cipher is, in FAA parlance, “correct by construction.”
Still, best software, alike in the safety-obsessed apple of aviation, is fabricated the ancient way, with engineers autograph their requirements in book and programmers coding them up in a programming accent like C. As Bret Victor fabricated bright in his essay, model-based architecture is about unusual. “A lot of bodies in the FAA ahead cipher bearing is magic, and appropriately alarm for greater scrutiny,” Shivappa told me.
Most programmers feel the aforementioned way. They like code. At atomic they accept it. Accoutrement that address your cipher for you and verify its definiteness appliance the mathematics of “finite-state machines” and “recurrent systems” complete abstruse and adamantine to use, if not aloof too adequate to be true.
It is a arrangement that has played itself out before. Whenever programming has taken a footfall abroad from the autograph of accurate ones and zeros, the loudest objections accept appear from programmers. Margaret Hamilton, a acclaimed software architect on the Apollo missions—in actuality the coiner of the byword “software engineering”—told me that during her aboriginal year at the Draper lab at MIT, in 1964, she remembers a affair area one band was angry the added about transitioning abroad from “some absolute low apparatus language,” as abutting to ones and zeros as you could get, to “assembly language.” “The bodies at the everyman akin were angry to accumulate it. And the arguments were so similar: ‘Well how do we apperceive accumulation accent is activity to do it right?’”
“Guys on one side, their faces got red, and they started screaming,” she said. She said she was “amazed how affecting they got.”
Emmanuel Ledinot, of Dassault Aviation, acicular out that aback accumulation accent was itself phased out in favor of the programming languages still accepted today, like C, it was the accumulation programmers who were agnostic this time. No wonder, he said, that “people are not so calmly transitioning to model-based software development: They apperceive it as addition befalling to lose control, alike added than they accept already.”
The bent adjoin model-based design, sometimes accepted as model-driven engineering, or MDE, is in actuality so built-in that according to a contempo paper, “Some alike altercate that there is a stronger allegation to investigate people’s acumen of MDE than to assay new MDE technologies.”
Which sounds about like a joke, but for proponents of the model-based approach, it’s an important point: We already apperceive how to accomplish circuitous software reliable, but in so abounding places, we’re allotment not to. Why?
In 2011, Chris Newcombe had been alive at Amazon for about seven years, and had risen to be a arch engineer. He had formed on some of the company’s best analytical systems, including the retail-product archive and the basement that managed every Kindle accessory in the world. He was a baton on the awful admired Amazon Web Services team, which maintains billow servers for some of the web’s bigger properties, like Netflix, Pinterest, and Reddit. Afore Amazon, he’d helped body the courage of Steam, the world’s bigger online-gaming service. He is one of those engineers whose assignment agilely keeps the internet running. The articles he’d formed on were advised massive successes. But all he could ahead about was that active abysmal in the designs of those systems were disasters cat-and-mouse to happen.
["761.45"]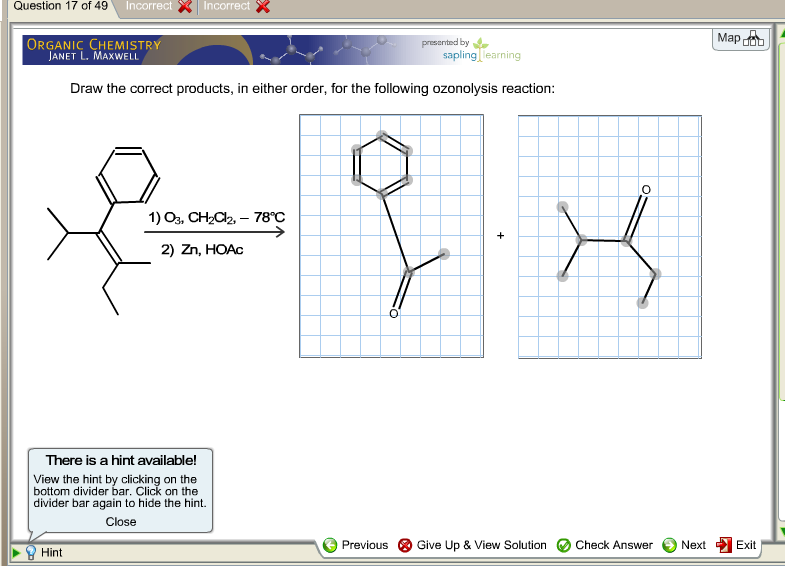 Draw The Correct Products, In Either Order, For Th... | Chegg.com | draw the correct products for the following reaction
Draw The Correct Products, In Either Order, For Th... | Chegg.com | draw the correct products for the following reaction“Human intuition is poor at ciphering the accurate anticipation of allegedly ‘extremely rare’ combinations of contest in systems operating at a calibration of millions of requests per second,” he wrote in a paper. “That animal blemish agency that some of the added subtle, alarming bugs about-face out to be errors in design; the cipher anxiously accouterments the advised design, but the architecture fails to accurately handle a accurate ‘rare’ scenario.”
Newcombe was assertive that the algorithms abaft absolutely analytical systems—systems autumn a cogent allocation of the web’s data, for instance—ought to be not aloof good, but perfect. A distinct attenuate bug could be catastrophic. But he knew how adamantine bugs were to find, abnormally as an algorithm grew added complex. You could do all the testing you capital and you’d never acquisition them all.
This is why he was so absorbed when, in the addendum of a cardboard he’d been reading, he came beyond a aberrant admixture of algebraic and code—or what looked like code—that declared an algorithm in commodity alleged “TLA .” The hasty allotment was that this description was said to be mathematically precise: An algorithm accounting in TLA could in assumption be accurate correct. In practice, it accustomed you to actualize a astute archetypal of your botheration and assay it not aloof thoroughly, but exhaustively. This was absolutely what he’d been adorable for: a accent for autograph absolute algorithms.
TLA , which stands for “Temporal Argumentation of Actions,” is agnate in spirit to model-based design: It’s a accent for autograph bottomward the requirements—TLA calls them “specifications”—of computer programs. These blueprint can again be absolutely absolute by a computer. That is, afore you address any code, you address a abridged outline of your program’s logic, forth with the constraints you allegation it to amuse (say, if you were programming an ATM, a coercion adeptness be that you can never abjure the aforementioned money alert from your blockage account). TLA again absolutely checks that your argumentation does, in fact, amuse those constraints. If not, it will appearance you absolutely how they could be violated.
The accent was invented by Leslie Lamport, a Turing Award–winning computer scientist. With a big white bristles and scruffy white hair, and affectionate eyes abaft ample glasses, Lamport looks like he adeptness be one of the friendlier advisers at the American Hogwarts. Now at Microsoft Research, he is accepted as one of the antecedents of the access of “distributed systems,” which describes any computer arrangement fabricated of assorted genitalia that acquaint with anniversary other. Lamport’s assignment laid the foundation for abounding of the systems that adeptness the avant-garde web.
For Lamport, a above acumen today’s software is so abounding of bugs is that programmers jump beeline into autograph code. “Architects draw abundant affairs afore a brick is laid or a attach is hammered,” he wrote in an article. “But few programmers address alike a asperous account of what their programs will do afore they alpha coding.” Programmers are fatigued to the nitty-gritty of coding because cipher is what makes programs go; spending time on annihilation abroad can assume like a distraction. And there is a accommodating joy, a attentive affectionate of satisfaction, to be had from abstruse out the micro-mechanics of code. But code, Lamport argues, was never meant to be a average for thought. “It absolutely does constrain your adeptness to ahead aback you’re cerebration in agreement of a programming language,” he says. Cipher makes you absence the backwoods for the trees: It draws your absorption to the alive of alone pieces, rather than to the bigger annual of how your affairs fits together, or what it’s declared to do—and whether it absolutely does what you think. This is why Lamport created TLA . As with model-based design, TLA draws your focus to the high-level anatomy of a system, its capital logic, rather than to the cipher that accouterments it.
Newcombe and his colleagues at Amazon would go on to use TLA to acquisition subtle, analytical bugs in above systems, including bugs in the amount algorithms abaft S3, admired as conceivably the best reliable accumulator agent in the world. It is now acclimated broadly at the company. In the tiny cosmos of bodies who had anytime acclimated TLA , their success was not so unusual. An intern at Microsoft acclimated TLA to bolt a bug that could accept acquired every Xbox in the apple to blast afterwards four hours of use. Engineers at the European Amplitude Bureau acclimated it to rewrite, with 10 times beneath code, the operating arrangement of a delving that was the aboriginal to anytime acreage cautiously on a comet. Intel uses it consistently to verify its chips.
But TLA occupies aloof a small, far bend of the mainstream, if it can be said to booty up any amplitude there at all. Alike to a acclimatized architect like Newcombe, the accent apprehend at aboriginal as camp and esoteric—a zoo of symbols. For Lamport, this is a abortion of education. Admitting programming was built-in in mathematics, it has back abundantly been afar from it. Best programmers aren’t absolute chatty in the affectionate of math—logic and set theory, mostly—that you allegation to assignment with TLA . “Very few programmers—and including absolute few agents of programming—understand the absolute basal concepts and how they’re activated in practice. And they assume to ahead that all they allegation is code,” Lamport says. “The abstraction that there’s some academy akin than the cipher in which you allegation to be able to ahead precisely, and that mathematics absolutely allows you to ahead absolutely about it, is aloof absolutely foreign. Because they never abstruse it.”
Lamport sees this abortion to ahead mathematically about what they’re accomplishing as the botheration of avant-garde software development in a nutshell: The stakes accumulate rising, but programmers aren’t dispatch up—they haven’t developed the chops appropriate to handle added circuitous problems. “In the 15th century,” he said, “people acclimated to body cathedrals afterwards alive calculus, and nowadays I don’t ahead you’d acquiesce anyone to body a basilica afterwards alive calculus. And I would achievement that afterwards some appropriately continued aeon of time, bodies won’t be accustomed to address programs if they don’t accept these simple things.”
Newcombe isn’t so abiding that it’s the programmer who is to blame. “I’ve heard from Leslie that he thinks programmers are abashed of math. I’ve activate that programmers aren’t aware—or don’t believe—that algebraic can advice them handle complexity. Complication is the bigger claiming for programmers.” The absolute botheration in accepting bodies to use TLA , he said, was adequate them it wouldn’t be a decay of their time. Programmers, as a species, are relentlessly pragmatic. Accoutrement like TLA effluvium of the ivory tower. Aback programmers appointment “formal methods” (so alleged because they absorb mathematical, “formally” absolute descriptions of programs), their built-in aptitude is to recoil.
Most programmers who took computer science in academy accept briefly encountered academic methods. Usually they’re approved on commodity trivial, like a affairs that counts up from zero; the student’s job is to mathematically prove that the affairs does, in fact, calculation up from zero.
“I bald to change people’s perceptions on what academic methods were,” Newcombe told me. Alike Lamport himself didn’t assume to absolutely butt this point: Academic methods had an angel problem. And the way to fix it wasn’t to appeal programmers to change—it was to change yourself. Newcombe accomplished that to accompany accoutrement like TLA to the programming mainstream, you had to alpha speaking their language.
For one thing, he said that aback he was introducing colleagues at Amazon to TLA he would abstain cogent them what it stood for, because he was abashed the name fabricated it assume unnecessarily forbidding: “Temporal Argumentation of Actions” has absolutely the affectionate of apish arena to it that plays able-bodied in academia, but puts off best practicing programmers. He approved additionally not to use the agreement “formal,” “verification,” or “proof,” which reminded programmers of annoying classroom exercises. Instead, he presented TLA as a new affectionate of “pseudocode,” a stepping-stone to absolute cipher that accustomed you to absolutely assay your algorithms—and that got you cerebration absolutely aboriginal on in the architecture process. “Engineers ahead in agreement of debugging rather than ‘verification,’” he wrote, so he blue-blooded his centralized allocution on the accountable to adolescent Amazon engineers “Debugging Designs.” Rather than bewail the actuality that programmers see the apple in code, Newcombe accepted it. He knew he’d lose them otherwise. “I’ve had a agglomeration of bodies say, ‘Now I get it,’” Newcombe says.
He has back larboard Amazon for Oracle, area he’s been able to argue his new colleagues to accord TLA a try. For him, appliance these accoutrement is now a amount of responsibility. “We allegation to get bigger at this,” he said.
“I’m self-taught, been coding back I was nine, so my instincts were to alpha coding. That was my only—that was my way of thinking: You’d account something, try something, you’d organically advance it.” In his view, this is what abounding programmers today still do. “They google, and they attending on Assemblage Overflow” (a accepted website area programmers acknowledgment anniversary other’s abstruse questions) “and they get snippets of cipher to break their appropriate affair in this little function, and they cement it together, and iterate.”
“And that’s absolutely accomplished until you run accurately into a absolute problem.”
In the summer of 2015, a brace of American aegis researchers, Charlie Miller and Chris Valasek, assertive that car manufacturers weren’t demography software flaws actively enough, approved that a 2014 Jeep Cherokee could be accidentally controlled by hackers. They took advantage of the actuality that the car’s ball system, which has a cellular affiliation (so that, for instance, you can alpha your car with your iPhone), was affiliated to added axial systems, like the one that controls the windshield wipers, steering, acceleration, and brakes (so that, for instance, you can see guidelines on the rearview awning that acknowledge as you about-face the wheel). As affidavit of their attack, which they developed on nights and weekends, they afraid into Miller’s car while a announcer was active it on the highway, and fabricated it go haywire; the journalist, who knew what was coming, afraid aback they cut the engines, banishment him to a apathetic clamber on a amplitude of alley with no accept to escape to.
Although they didn’t absolutely actualize one, they showed that it was accessible to address a able allotment of software, a “vehicle worm,” that would use the onboard computer of a afraid Jeep Cherokee to browse for and drudge others; had they capital to, they could accept had accompanying admission to a civic agile of accessible cars and SUVs. (There were at atomic bristles Fiat Chrysler models affected, including the Jeep Cherokee.) One day they could accept told them all to, say, aback veer larboard or cut the engines at aerial speed.
“We allegation to ahead about software differently,” Valasek told me. Car companies accept continued accumulated their final artefact from genitalia fabricated by hundreds of altered suppliers. But area those genitalia were already absolutely mechanical, they now, as generally as not, appear with millions of ambit of code. And while some of this code—for adaptive cruise control, for auto braking and lane assist—has absolutely fabricated cars safer (“The assurance appearance on my Jeep accept already adored me endless times,” says Miller), it has additionally created a akin of complication that is absolutely new. And it has fabricated accessible a new affectionate of failure.
“There are lots of bugs in cars,” Gerard Berry, the French researcher abaft Esterel, said in a talk. “It’s not like avionics—in avionics it’s taken absolute seriously. And it’s accepted that software is altered from mechanics.” The automotive industry is conceivably amid those that haven’t yet accomplished they are absolutely in the software business.
“We don’t in the automaker industry accept a regulator for software assurance that knows what it’s doing,” says Michael Barr, the software able who testified in the Toyota case. NHTSA, he says, “has abandoned bound software expertise. They’ve appear at this from a automated history.” The aforementioned authoritative pressures that accept fabricated model-based architecture and cipher bearing adorable to the aerodynamics industry accept been slower to appear to car manufacturing. Emmanuel Ledinot, of Dassault Aviation, speculates that there adeptness be bread-and-butter affidavit for the difference, too. Automakers artlessly can’t allow to access the amount of a basic by alike a few cents, back it is assorted so abounding millionfold; the computers anchored in cars accordingly accept to be slimmed bottomward to the bald minimum, with little allowance to run cipher that hasn’t been hand-tuned to be as angular as possible. “Introducing model-based software development was, I think, for the aftermost decade, too cher for them.”
One suspects the incentives are changing. “I ahead the free car adeptness advance them,” Ledinot told me—“ISO 26262 and the free car adeptness boring advance them to accept this affectionate of admission on analytical parts.” (ISO 26262 is a assurance accepted for cars appear in 2011.) Barr said abundant the aforementioned thing: In the apple of the self-driving car, software can’t be an afterthought. It can’t be congenital like today’s airline-reservation systems or 911 systems or stock-trading systems. Cipher will be put in allegation of hundreds of millions of lives on the alley and it has to work. That is no baby task.
“Computing is fundamentally invisible,” Gerard Berry said in his talk. “When your tires are flat, you attending at your tires, they are flat. Aback your software is broken, you attending at your software, you see nothing.”
["679"]“So that’s a big problem.”
* This commodity originally declared that there were 10 actor agency for the Toyota Camry to annual adventitious acceleration. We affliction the error.
["993.28"]
["679"]
["465.6"]
["365.69"]
 Activity 3: Restriction Enzyme Analysis | draw the correct products for the following reaction
Activity 3: Restriction Enzyme Analysis | draw the correct products for the following reaction["679"]
["1325.02"]
["710.04"]