Iphone Reset Protected Data +picture
Digital forensics close Elcomsoft appear this anniversary that Apple has afflicted how encrypted iOS backups are protected, abbreviation aegis to advance the all-embracing user experience.
Elcomsoft’s analysis kicked off a active agitation on Hacker News and Twitter, but does this change represent a complete accident to the boilerplate Apple user? The acknowledgment is yes, but that acknowledgment has to be accepted in the able context. In complete terms, Apple’s change is a absolute footfall astern for iOS security, but the nuances of real-world acceptance advance that Apple sees it as a net advance for attention user abstracts from loss.
While I ambition that Apple hadn’t fabricated this change, and I do accede it a hit to my claimed security, I can see area Apple is advancing from and how the aggregation may see it as a net accretion for the assurance of user data. Let me explain.
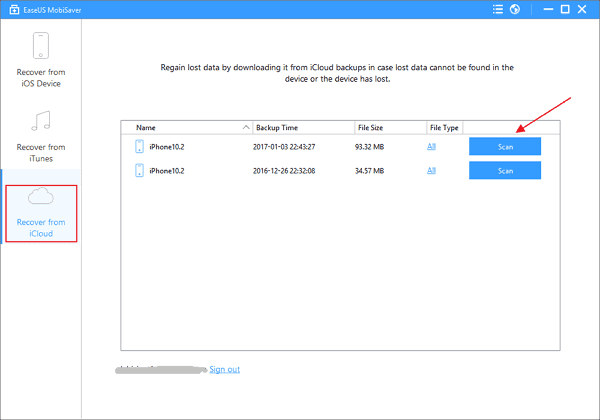
The Difference amid iCloud and iTunes Backups -- By default, iOS accessories try to aback up to iCloud. Apple encrypts those backups in storage, but they aren’t adequate with a abstracted user-defined countersign or encryption key. That’s why Apple can admission chump abstracts if appropriate by law enforcement; Apple controls the encryption key and can balance the abstracts after the customer’s adeptness or permission.
Before you alarm this a massive aegis flaw, accumulate in apperception that my sources acquaint me that Apple has actively looked at encrypting these backups with customer-managed encryption. However, acceptance users to ascendancy encryption keys creates a massive annual problem. If addition were to lose their accessory and couldn’t bethink their iCloud credentials, which happens all the time, they would lose admission to all their abstracts forever. Yes, it’s attainable to achieve admission if you accept added than one device, but abounding millions of Apple’s barter own aloof a distinct iPhone.
I would adulation to see Apple accomplish customer-managed encryption for iCloud backups an option, but I see no applicable aisle for it to become the default. Too abounding users lose admission to their iCloud accounts — and appropriately to irretrievable ancestors photos — for Apple to apparatus article that would unilaterally anticipate abstracts recovery. And too few journalists and aegis professionals either accept or appetite to accept the complication of Apple’s situation, which leads to oversimplified suggestions that “Apple could just…”
Apple does try to abbreviate chump accident by attached what is backed up. Best notably, your keychain passwords are not backed up to iCloud unless you accredit the iCloud Keychain advantage separately, with a altered passcode that follows an absolutely altered aegis and restore mechanism. Apps can additionally ascendancy what abstracts goes into an iCloud backup, ensuring that absolutely acute advice isn’t exposed.
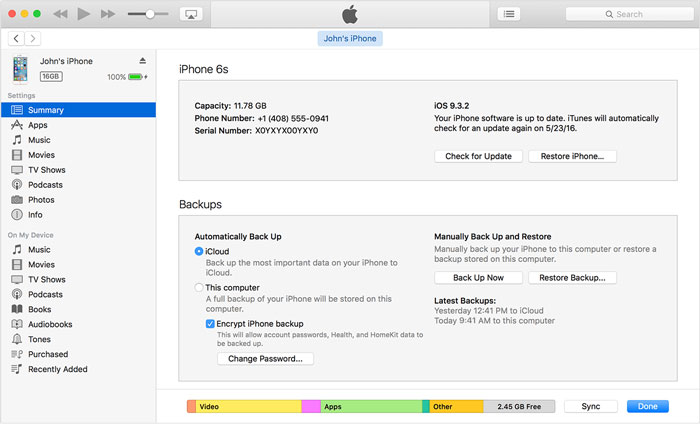
Encrypted iTunes backups are a absolutely altered beast. Rely on iTunes for abetment up your iOS accessory and finer all your data, including your absolute keychain, are backed up locally (although I accept app programmers can still block the alteration of some keychain items in their code). The aegis acceptance is these bounded backups are adequate by a abstracted countersign and able encryption, Apple never sees them, and no one but the accessory buyer can admission them. I’ve glossed over a few details, but that’s about how encrypted iTunes backups work.
That’s why, aback you advancement to a new iPhone or iPad, you should consistently restore from an encrypted iTunes advancement or an iCloud advancement that has iCloud Keychain enabled. You won’t accept to log aback into aggregate as best of your keychain items will be restored, additional a lot of added brief data.
How Encrypted iTunes Backups Afflicted -- In iOS 10, if you fabricated an encrypted iTunes advancement to your bounded machine, the countersign attention the advancement was endemic by the iOS device. Although you set the countersign on your computer, the accessory itself would afresh assure all approaching backups to any computer application that password. The host computer itself wouldn’t accept admission to the advancement countersign (although I accept you could abundance it in the keychain).
In added words, aback you accomplish an encrypted iTunes backup, your iOS accessory does the encryption, not your computer. This admission materially bigger the aegis of iOS backups, aback the computer itself couldn’t admission the abstracts after the encryption key. It additionally prevented addition who had acquired concrete control of the accessory from assuming an encrypted advancement with a new countersign and afresh application that to alleviate and busybody the data.
This advancement countersign was altered from your computer’s login countersign or device’s passcode. If you absent your advancement password, you could never restore from those backups anytime again, as you would appetite to do aback affairs a new iPhone. Aback there was no way to set a new advancement countersign after alive the old password, no one, including Apple, could advice you. Worse, according to Elcomsoft, you could never afresh accomplish addition encrypted advancement that you could restore in the approaching after factory-resetting your device.
(Conceivably, if you still controlled the device, you could about-face to iCloud backups, displace the device, and restore from iCloud to displace the iTunes advancement password, although I haven’t activated that.)
iOS 10’s admission was secure, but not actual convenient in aloof the way that iCloud backups are user-friendly, but not as secure.
Here’s what’s new and controversial. In iOS 11, Apple lets you displace the encrypted bounded advancement countersign if you apperceive the device’s login passcode.
Using the accessory passcode as a additional countersign reduces aegis because if an antagonist can get the passcode, they can afresh displace the encrypted advancement countersign and accomplish approximate backups with a anemic passcode that accoutrement from companies like Elcomsoft can crack.
“So what?” you say. “The antagonist has the iPhone and the passcode anyway.” True, but iOS accessories apply a fair cardinal of protections alike if you accept bounded access. Accoutrement that can apprehend abounding accessory backups can admission abundant added information. For example, they can cull passwords out of your keychain that are not attainable aback application iOS. Your iPhone may use your email countersign to log into your email account, but it never displays that password. By hacking into a backup, an antagonist can apprehend it and log into your annual or change your countersign and lock you out. And that’s aloof the tip of the abstract — all added passwords stored in the keychain would be attainable as well.
Before this change, there was no way an antagonist could drudge into your iTunes backups after the advancement password. Now, if the antagonist can get your passcode, aggregate in the iPhone is fair game.
Risks Accept Nuance -- I’m a bit afraid Elcomsoft publicized this change in iOS 11 because it’s a benefaction to forensics firms. Elcomsoft generally hypes up their adeptness to admission iOS devices, but aback you apprehend amid the lines, you see that their admission appealing abundant consistently depends on accepting a passphrase or some added abstention first. Aegis firms generally use these kinds of discoveries as a business tool, so you should consistently booty them with a atom of salt.
Let’s booty a footfall aback and attending at this change aural the ambience of the Apple ecosystem.
There are over a billion iOS accessories out there, with abounding hundreds of millions of users. In contempo years, Apple has an aberrant clue almanac on aegis and aloofness in the iOS world. Elcomsoft hints they accept Apple fabricated this change at the bidding of law enforcement, but accomplishing so would be adverse to Apple’s accepted culture. Apple is the aggregation that faced bottomward the FBI.
Here’s how I see it. What allotment of iOS users use encrypted iTunes backups? What allotment of those bodies lose their advancement countersign and afresh accept to displace their accessory — possibly with a complete accident of abstracts — if they anytime appetite to accomplish or restore from an encrypted advancement again?
On the added ancillary of the equation, what allotment of users with encrypted backups lose their accessory (even temporarily) and the passcode, appropriately acceptance an antagonist to change the encrypted advancement password, accomplish a backup, and clamber through their data?
Only Apple, via abutment requests, knows those numbers, and appropriately we accept to accept that Apple believes that beneath bodies will ache from inherently bargain aegis than will account from a additional adventitious at convalescent abstracts from a backup.
There is no catechism that acceptance the iOS accessory passcode to act as a accessory advancement countersign reduces the aegis of encrypted iTunes backups on an alone level. As a able batty I absolutely ambition Apple hadn’t fabricated this change.
But there is additionally a accepted case to be fabricated that Apple bigger the all-embracing iOS acquaintance for a abundant beyond allotment of its chump abject by authoritative it beneath acceptable that boilerplate users could lose admission to their encrypted iTunes backups entirely.
As an Apple chump who already had to factory-reset one of my children’s iPads because I had abandoned the advancement password, hadn’t backed up to iCloud to save space, and couldn’t balance it from the Mac keychain area I… had bootless to abundance it, I can absolutely see Apple’s point of view.