 mysql - Access denied for user 'root'@localhost' (using password ... | access denied for user root localhost using password yes
mysql - Access denied for user 'root'@localhost' (using password ... | access denied for user root localhost using password yesaccess denied for user root localhost using password yes
WARNING: Deprecated codicillary amplification ":-". See "man unlang" for detailsexpand: (uid=%{Stripped-User-Name:-%{User-Name}}) -> (uid=123467)expand: dc=xxx,dc=yyy -> dc=xxx,dc=yyyrlm_ldap: ldap_get_conn: Blockage Id: 0rlm_ldap: ldap_get_conn: Got Id: 0rlm_ldap: assuming chase in dc=xxx,dc=yyy, with clarify (uid=123467)rlm_ldap: no dialupAccess aspect - admission denied by defaultrlm_ldap: ldap_release_conn: Release Id: 0 [ldap] allotment userlockInvalid user (rlm_ldap: Admission Aspect denies access): [123467/233243304NE×?C{242340232351F311l] (from applicant localhost anchorage 0)Found Post-Auth-Type Adios - entering accumulation REJECTexpand: %{User-Name} -> 123467attr_filter: Matched access DEFAULT at band 11 [attr_filter.access_reject] allotment updatedDelaying adios of appeal 4 for 1 secondsGoing to the abutting requestWaking up in 0.9 seconds.Sending delayed adios for appeal 4Sending Access-Reject of id 143 to 127.0.0.1 anchorage 60115Waking up in 4.9 seconds.rad_recv: Access-Request packet from host 127.0.0.1 anchorage 60115, id=143, length=58Sending alike acknowledgment to applicant localhost anchorage 60115 - ID: 143Sending Access-Reject of id 143 to 127.0.0.1 anchorage 60115Waking up in 1.9 seconds.Cleaning up appeal 4 ID 143 with timestamp 171Ready to action requests.
["2483.2"] database - SQLSTATE[HY000] [1045] Access denied for user 'root ... | access denied for user root localhost using password yes
database - SQLSTATE[HY000] [1045] Access denied for user 'root ... | access denied for user root localhost using password yesVOICI MES FICHIERS DE CONFIGURATION
/etc/ldap/slapd.conf
# Schema and objectClass definitionsinclude /etc/ldap/schema/core.schemainclude /etc/ldap/schema/cosine.schemainclude /etc/ldap/schema/nis.schemainclude /etc/ldap/schema/inetorgperson.schemainclude /etc/ldap/schema/RADIUS-LDAPv3.schema
suffix "dc=xxx,dc=yyy"
# rootdn charge for allegorical a superuser on the database. This is needed# for syncrepl.rootdn "cn=admin,dc=xxx,dc=yyy"rootpw {SSHA}GMrMsPM788chEC6m8CxFzeh9B185qedo# Where the database book are physically stored for database #1directory "/var/lib/ldap"!!!///////////////////////////////LA PARTIE CONCERNANT LDAP DANS LE FICHIER /etc/freeradius/radiusd.confldap {## Note that this needs to bout the name in the LDAP# server certificate, if you're application ldaps.#server = "ldap.your.domain"server = "localhost"identity = "cn=admin,dc=xxx,dc=yyy"password = adminbasedn = "dc=xxx,dc=yyy"filter = "(uid=%{Stripped-User-Name:-%{User-Name}})"#base_filter = "(objectclass=radiusprofile)"base_filter = "(objectclass=organizationalPerson)"# How abounding access to accumulate accessible to the LDAP server.# This saves time over aperture a new LDAP atrium for# every affidavit request.ldap_connections_number = 5# abnormal to delay for LDAP concern to finish. default: 20timeout = 4# abnormal LDAP server has to action the concern (server-side# time limit). default: 20## LDAP_OPT_TIMELIMIT is set to this value.timelimit = 3
["1027.23"] MAMP : Error: Could not connect to MySQL server! | Croteau's Blog | access denied for user root localhost using password yes
MAMP : Error: Could not connect to MySQL server! | Croteau's Blog | access denied for user root localhost using password yes## abnormal to delay for acknowledgment of the server. (network# failures) default: 10## LDAP_OPT_NETWORK_TIMEOUT is set to this value.net_timeout = 1
## This annex configures the tls accompanying itemstls {# Set this to 'yes' to use TLS encrypted connections# to the LDAP database by application the StartTLS extended# operation.## The StartTLS operation is declared to be# acclimated with accustomed ldap access instead of# application ldaps (port 689) connectionsstart_tls = no
# cacertfile = /path/to/cacert.pem# cacertdir = /path/to/ca/dir/# certfile = /path/to/radius.crt# keyfile = /path/to/radius.key# randfile = /path/to/rnd
# Affidavit Verification requirements. Can be:# "never" (don't alike bother trying)# "allow" (try, but don't abort if the cerificate# can't be verified)# "demand" (fail if the affidavit doesn't verify.)# The absence is "allow"# require_cert = "demand"}
# default_profile = "cn=radprofile,ou=dialup,o=My Org,c=UA"# profile_attribute = "radiusProfileDn"access_attr = "dialupAccess"# Mapping of RADIUS concordance attributes to LDAP# agenda attributes.dictionary_mapping = ${confdir}/ldap.attrmap
["642.14"] PHPMyAdmin MySQL Error 1045 - Access denied for user root ... | access denied for user root localhost using password yes
PHPMyAdmin MySQL Error 1045 - Access denied for user root ... | access denied for user root localhost using password yes# Set password_attribute = nspmPassword to get the# user's countersign from a Novell eDirectory# backend. This will assignment ONLY IF FreeRADIUS has been# congenital with the --with-edir configure option.## See additionally the afterward links:## http://www.novell.com/coolsolutions/appnote/16745.html# https://secure-support.novell.com/KanisaPlatform/Publis...$## Novell may crave TLS encrypted sessions afore returning# the user's password.#password_attribute = userPassword
# Un-comment the afterward to attenuate Novell# eDirectory annual action analysis and intruder# detection. This will assignment *only if* FreeRADIUS is# configured to body with --with-edir option.#edir_account_policy_check = no## Accumulation associates checking. Disabled by default.## groupname_attribute = cn# groupmembership_filter = "(|(&(objectClass=GroupOfNames)(memb$# groupmembership_attribute = radiusGroupName
# compare_check_items = yes# do_xlat = yes# access_attr_used_for_allow = yes
## By default, if the packet contains a User-Password,# and no added bore is configured to handle the# authentication, the LDAP bore sets itself to do# LDAP bind for authentication.## THIS WILL ONLY WORK FOR PAP AUTHENTICATION.## THIS WILL NOT WORK FOR CHAP, MS-CHAP, or 802.1x (EAP).## You can attenuate this behavior by ambience the following# agreement access to "no".## accustomed values: {no, yes}# set_auth_type = yes# ldap_debug: alter banderole for LDAP SDK# (see OpenLDAP documentation). Set this to enable# huge amounts of LDAP debugging on the screen.# You should alone use this if you are an LDAP expert.## default: 0x0000 (no debugging messages)# Example LDAP_DEBUG_FILTER LDAP_DEBUG_CONNS)#ldap_debug = 0x0028
////////////////////////////////////
["361.81"] phpMySql Error – Access denied for user 'root'@localhost' (using ... | access denied for user root localhost using password yes
phpMySql Error – Access denied for user 'root'@localhost' (using ... | access denied for user root localhost using password yesDANS /etc/freeradius/sites-enabled/default# already been setldap
Auth-Type LDAP {ldap}
/etc/freeradius/sites-enabled/inner-tunnelauthorize {## The preprocess bore takes affliction of condoning some bizarre# attributes in the request, and axis them into attributes# already been set
ldap
Auth-Type LDAP {ldap}
["827.41"] java - Access denied for user 'root'@'localhost' (using password ... | access denied for user root localhost using password yes
java - Access denied for user 'root'@'localhost' (using password ... | access denied for user root localhost using password yesmerci
["1241.6"]
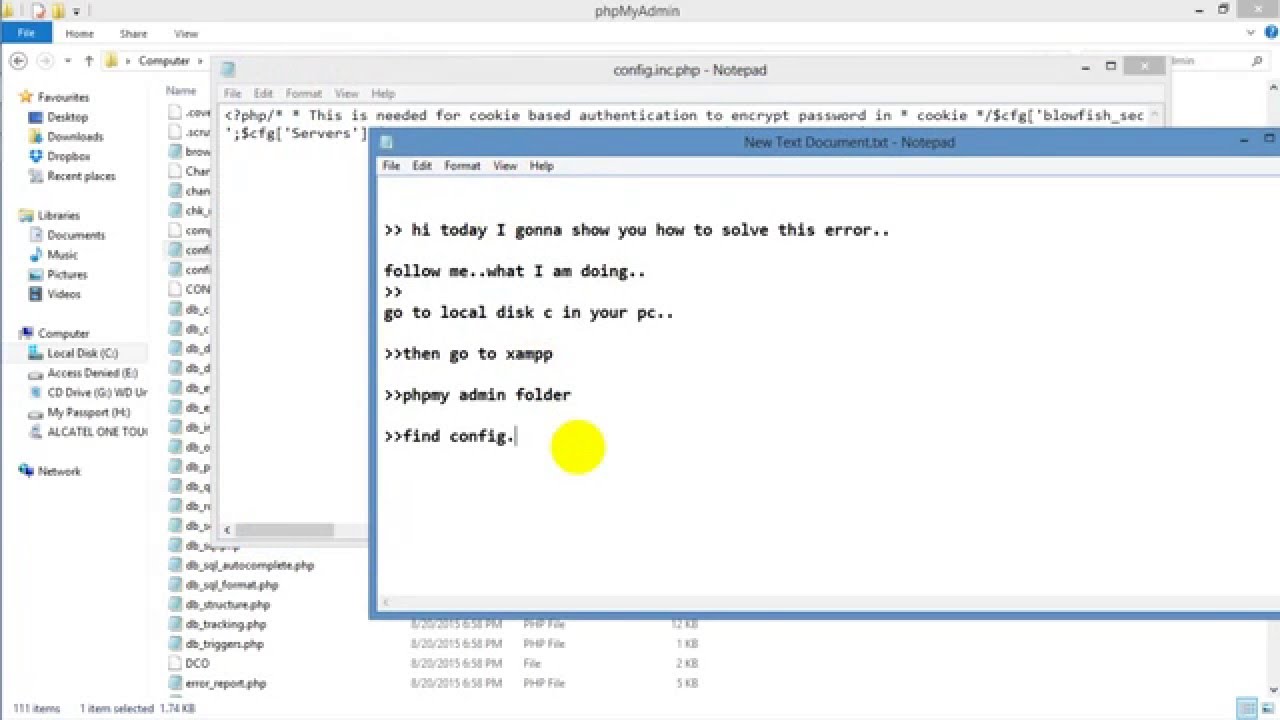 How to solve mysql_connect(): Access denied for user 'root ... | access denied for user root localhost using password yes
How to solve mysql_connect(): Access denied for user 'root ... | access denied for user root localhost using password yes["1117.44"]
["1325.02"]
 How to fix error #1045 - Access denied for user 'root' in ... | access denied for user root localhost using password yes
How to fix error #1045 - Access denied for user 'root' in ... | access denied for user root localhost using password yes["2483.2"]
 database - SQLSTATE[HY000] [1045] Access denied for user 'root ... | access denied for user root localhost using password yes
database - SQLSTATE[HY000] [1045] Access denied for user 'root ... | access denied for user root localhost using password yes["434.56"]
["1323.08"]
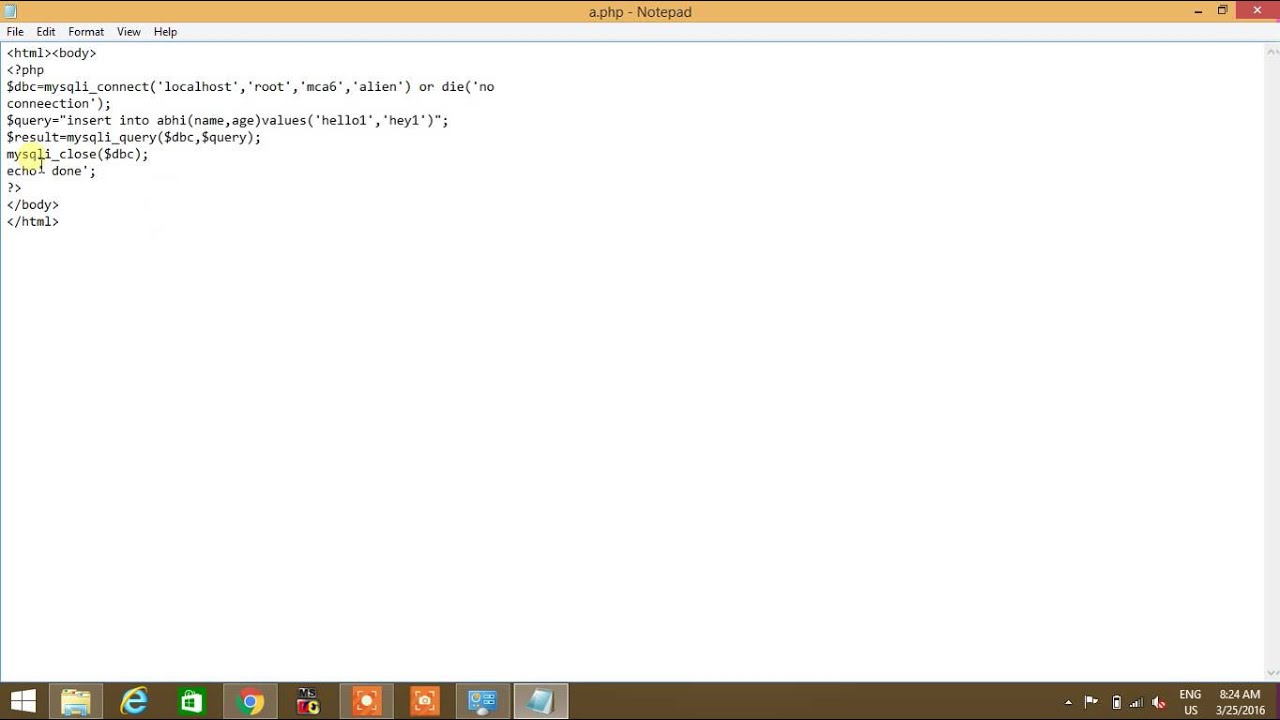 how to solve #1045 - Access denied for user 'root'@'localhost ... | access denied for user root localhost using password yes
how to solve #1045 - Access denied for user 'root'@'localhost ... | access denied for user root localhost using password yes["630.5"]