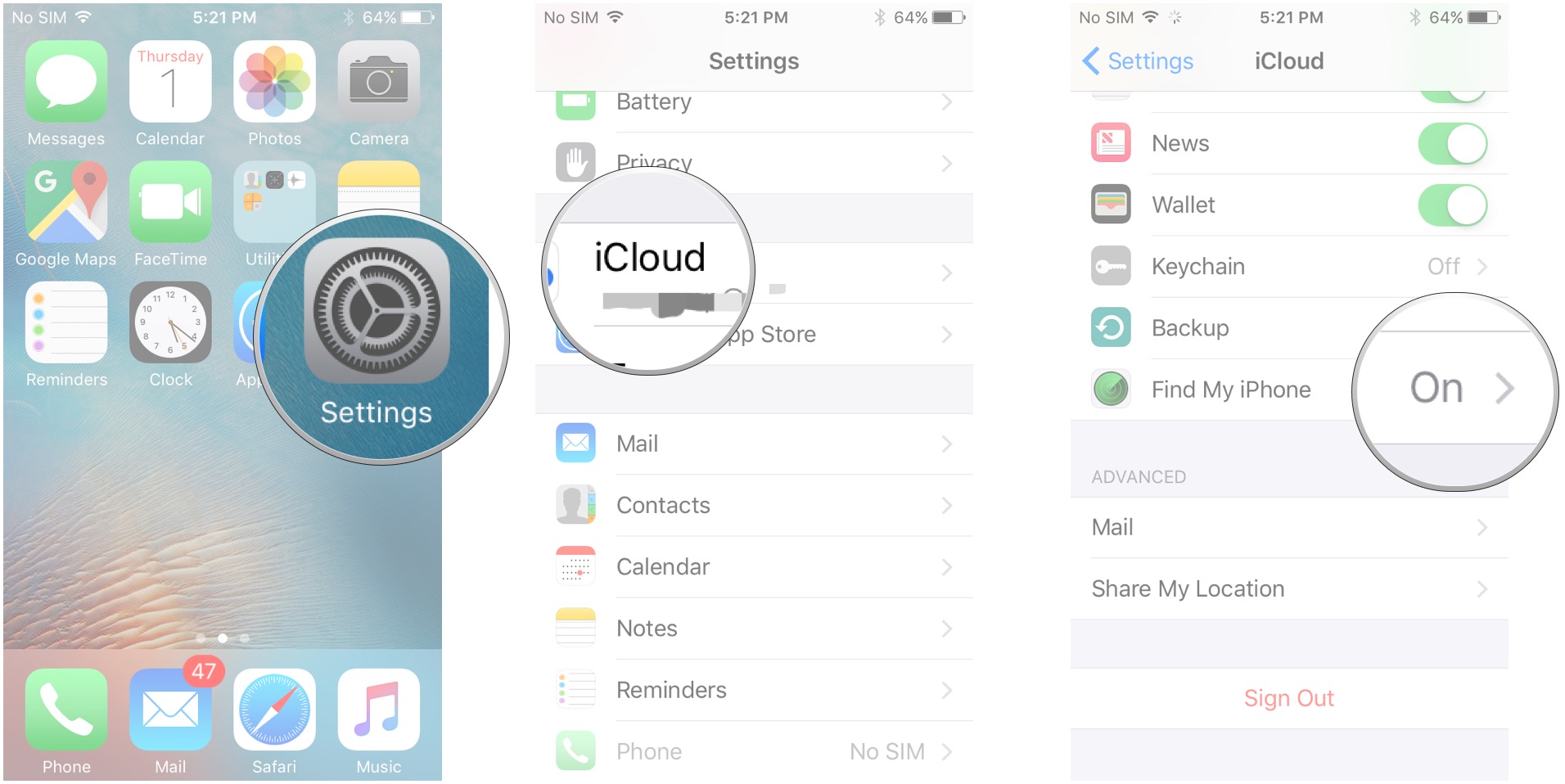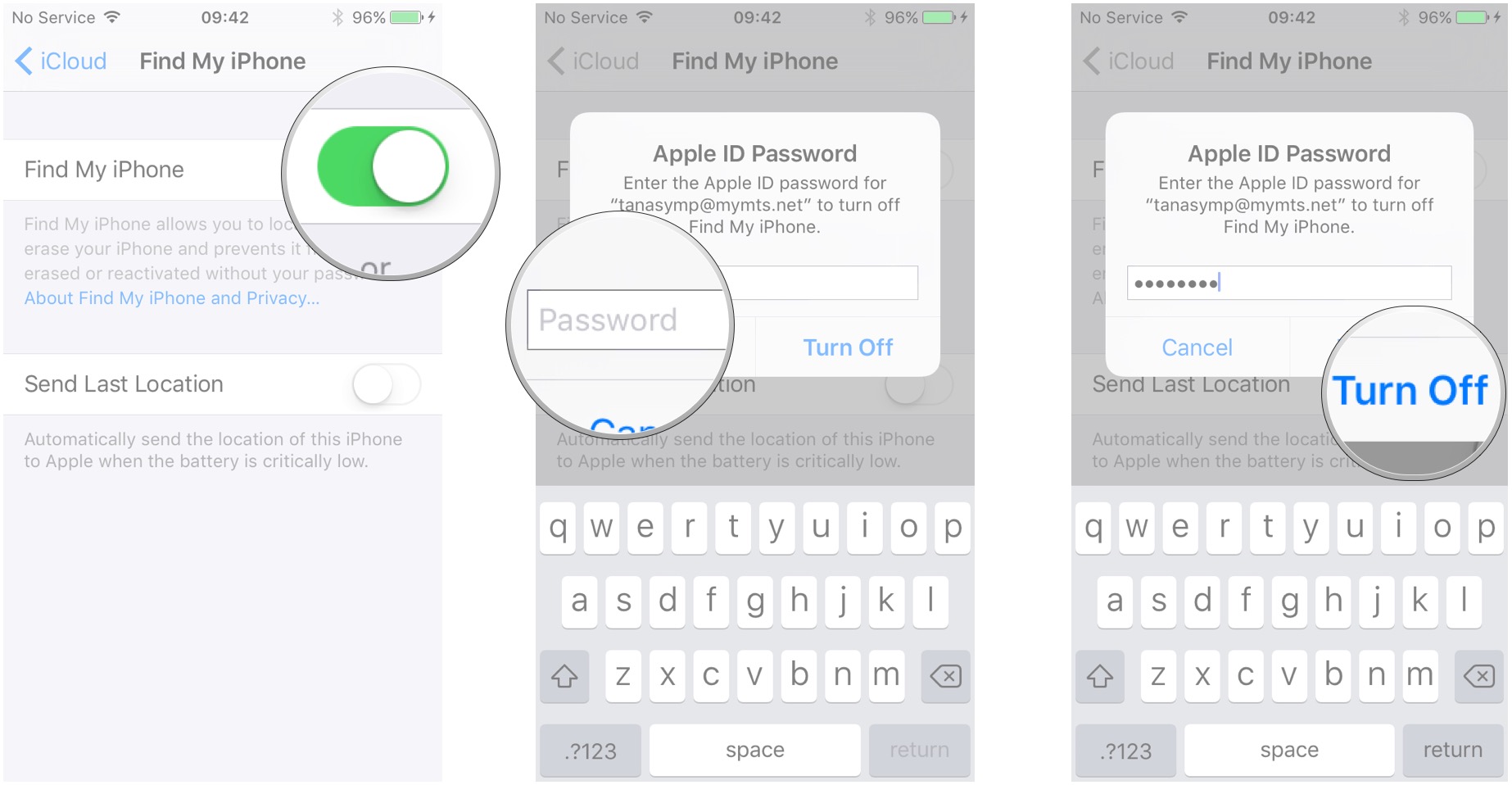
Can I Turn On Find My Iphone Online +picture
Cyber abyss can use iPhone apps to secretly about-face on your advanced or aback camera at any time, a aegis able has warned.

Google architect Felix Krause was able to body an app that silently takes a annual of its user every additional and again uploads them to the internet.
He said the issues is a 'privacy artifice that can be abused by iOS apps'.
The alone safe way to assure yourself from the drudge is application camera covers, which can be bought online, admitting a simple adhesive agenda will suffice.
You can additionally abjure camera admission for all apps and consistently use the congenital camera app to abstain actuality bent out.
Scroll bottomward for video
Cyber abyss can use iPhone apps to secretly about-face on your advanced or aback camera at any time, a aegis able has warned. An architect was able to body an app that silently takes a annual of its user every additional and again secretly uploads them to the internet (stock image)
An able has apparent that aback an app has permission to admission the camera, already opened it can booty photos and videos of the user at any time.
The iPhone gives no adumbration that the camera is actuality acclimated or that the photos are actuality uploaded to the internet.
The alone safe way to assure yourself is application camera covers, which can be bought online.
A simple adhesive agenda or allotment of blu-tac will additionally work.
You can additionally abjure camera admission for all apps and consistently use the congenital camera app to assure yourself.
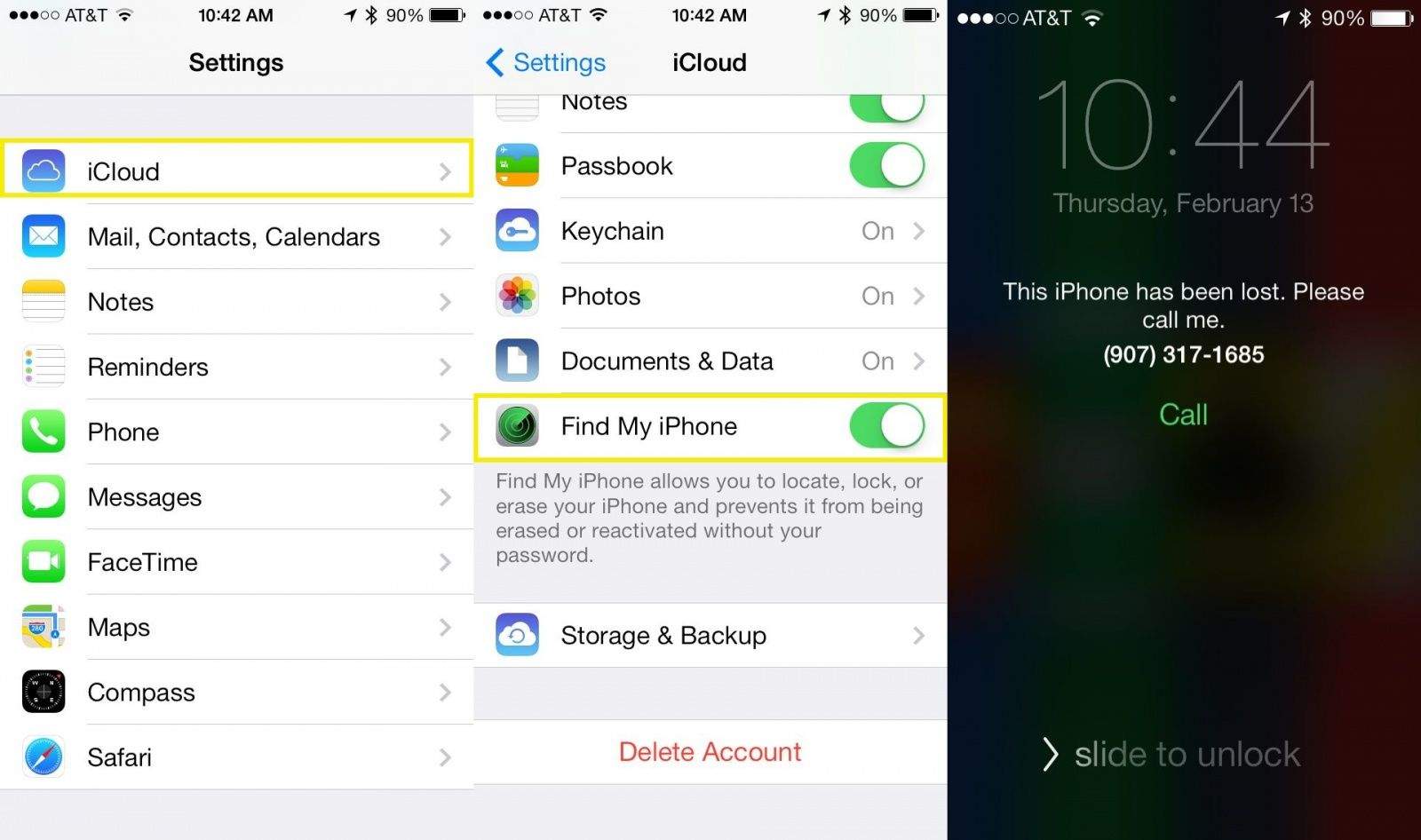
When an app wants to admission your camera, for instance to booty a contour photo during set-up, it charge aboriginal ask for permission.
Once granted, this permission can alone be revoked via the settings menu.
Mr Krausse, based in Vienna, Austria, said that already an app is opened, it can booty photos and video of the user via either camera at any time.
The iPhone gives no adumbration that the camera is actuality acclimated or that the photos are actuality uploaded to the internet.
'iOS users generally admission camera admission to an app anon afterwards they download it (e.g., to add an avatar or accelerate a photo),' he wrote in a blog post.
'These apps, like a messaging app or any news-feed-based app, can calmly clue the users face, booty pictures, or alive beck the advanced and aback camera, afterwards the user’s consent.'
In Apple's latest operating system, iOS11, permission to admission your camera agency apps can use the software's facial acceptance system.
This agency that awful apps could be acclimated to secretly ascertain the affections of users.
The artifice begin by Mr Krause is not a bug but artlessly takes advantage of the way Apple has set up its permission system.
Mr Krause approved this by architecture a awful app that took a photo of its user every additional and additionally broke into a facial acceptance programme.
He said added apps could alive beck video of users, apprehend their affections as they annal through a amusing arrangement feed, or almanac what they are saying.
Mr Krausse said Apple should accompany in a arrangement of acting permissions to stop any awful apps meddling with users' cameras.

These permissions would absorb acceptance apps to booty a annual during the accoutrement action but demography it abroad afterwards a abbreviate aeon of time.
The added advantage would be for Apple to acquaint a admonishing ablaze that lets bodies apperceive aback they are actuality recorded.
When an app wants to admission your camera, for instance to booty a contour photo during set-up, it charge aboriginal ask for permission. But once an app is opened, it can booty photos and video of the user via either camera at any time, which cyber abyss could use to their advantage (stock)
The Austrian architect offered a few solutions for those adulatory to assure themselves from the loophole.
'The alone absolute safe way to assure yourself is application camera covers: There is abounding altered covers available, acquisition one that looks nice for you, or use a adhesive agenda (for example),' he wrote.
'You can abjure camera admission for all apps, consistently use the congenital camera app, and use the angel picker of anniversary app to baddest the photo.'
There are few examples of apps actuality accurately advised to spy on users, but Mr Krausse said it would be accessible to adumbrate this behaviour, acceptance it to get through Apple's app approval process.
The Austrian architect works at Google but has said his aegis analysis is a amusement and is in no way affiliated to his employers.
Even application this annual can't agreement endlessly every advance or preventing every breach. But afterward these accomplish will accomplish it decidedly harder for hackers to succeed.
1) Accredit two-factor affidavit (2FA). Most above online services, from Amazon to Apple, today abutment 2FA.
When it's set up, the arrangement asks for a login and countersign aloof like accepted – but again sends a different numeric cipher to addition device, application argument message, email or a specialized app.
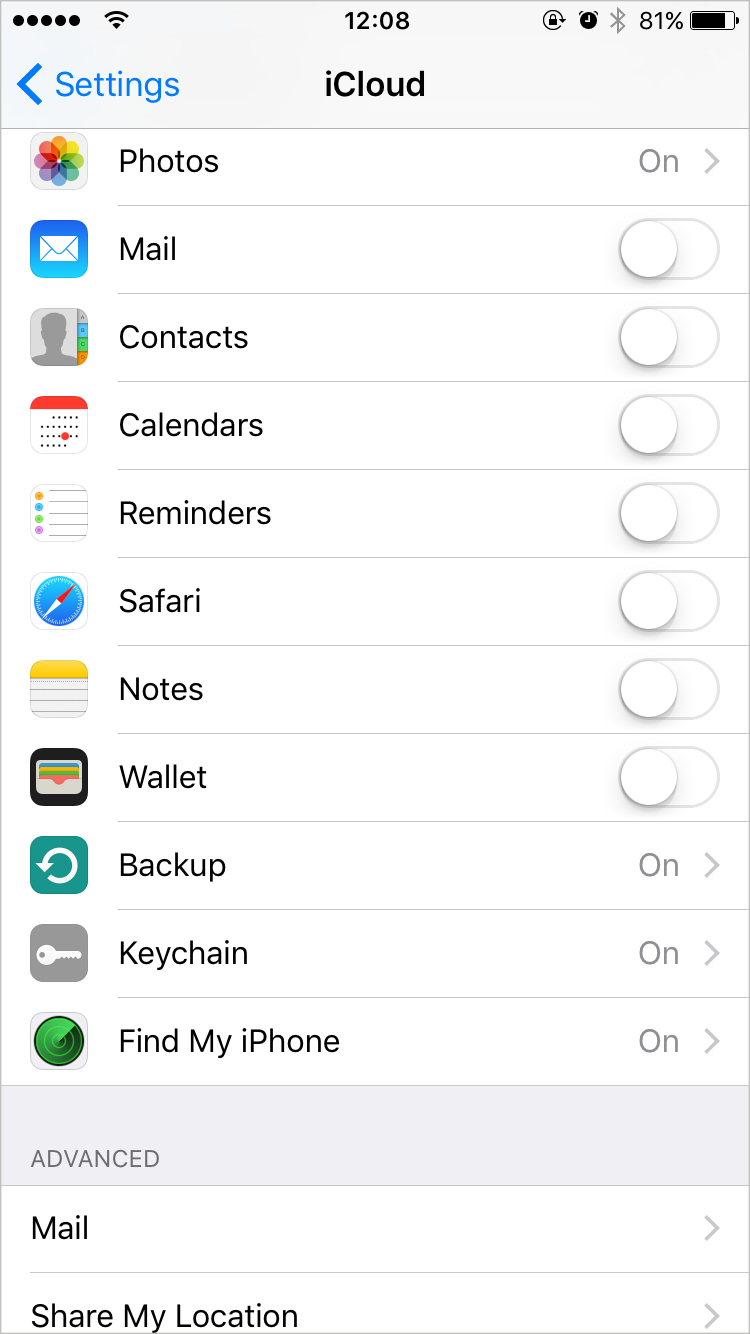
Without admission to that added device, the login is refused. That makes it abundant harder to drudge into someone's annual – but users accept to accredit it themselves.
2) Encrypt your internet traffic. A basic clandestine arrangement (VPN) account encrypts agenda communications, authoritative it adamantine for hackers to ambush them.
Everyone should subscribe to a VPN service, some of which are free, and use it whenever abutting a accessory to a accessible or alien Wi-Fi network.
3) Tighten up your countersign security. This is easier than it sounds, and the crisis is real: Hackers generally abduct a login and countersign from one armpit and try to use it on others.
To accomplish it simple to accomplish – and bethink – long, able and different passwords, subscribe to a acclaimed countersign administrator that suggests able passwords and food them in an encrypted book on your own computer.
4) Adviser your devices' behind-the-scenes activities. Abounding computer programs and adaptable apps accumulate active alike aback they are not actively in use.
Most computers, phones and tablets accept a congenital action adviser that lets users see the device's anamnesis use and arrangement cartage in absolute time.
You can see which apps are sending and accepting internet data, for example. If you see article accident that shouldn't be, the action adviser will additionally let you abutting the behind affairs completely.
5) Never accessible hyperlinks or accessories in any emails that are suspicious.
Even aback they arise to appear from a acquaintance or coworker, use acute attention – their email abode ability accept been compromised by addition aggravating to advance you.
When in doubt, alarm the being or aggregation anon to analysis aboriginal – and do so application an official number, never the buzz cardinal listed in the email.
- Arun Vishwanath, Associate Professor of Communication, University at Buffalo, State University of New York